vigo shower base installation instructionsbc kutaisi vs energy invest rustavi
- Posted by
- on Jul, 15, 2022
- in computer science monash handbook
- Blog Comments Off on vigo shower base installation instructions
 The Data Link Layer provides node-to-node data transfer (between two directly connected nodes), and also handles error correction from the physical layer. Neither of these protocols have anything to do with reservations. OSI model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications. Aruba service overlays existing infrastructure with virtual networks, Arista bundles edge networking gear for small enterprises. The first letter of each word is the same as the first letter an OSI layer. In the early- and mid-1970s, networking was largely either government-sponsored (NPL network in the UK, ARPANET in the US, CYCLADES in France) or vendor-developed with proprietary standards, such as IBM's Systems Network Architecture and Digital Equipment Corporation's DECnet. In the 1980s, the model became a working product of the Open Systems Interconnection group at the International Organization for Standardization (ISO). This made implementation difficult and was resisted by many vendors and users with significant investments in other network technologies. In addition, the OSI model can be used to understand cloud infrastructure migrations, particularly when it comes to securing data within the cloud. Examples of protocols are IP and Ipv6. Instead the layer facilitates communication through lower layers in order to establish connections with applications at the other end. It is a standard protocol that allows the systems to communicate over the internet. Communication protocols enable an entity in one host to interact with a corresponding entity at the same layer in another host. In the OSI reference model, the communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.[2]. The best known example of the Transport Layer is the Transmission Control Protocol (TCP), which is built on top of the Internet Protocol (IP), commonly known as TCP/IP. The Presentation layer is also known as the syntax layer. Specific examples of cross-layer functions include the following: Neither the OSI Reference Model, nor any OSI protocol specifications, outline any programming interfaces, other than deliberately abstract service descriptions. Streaming media, real-time multiplayer games and voice over IP (VoIP) are examples of applications in which loss of packets is not usually a fatal problem. RFC3439 contains a section entitled "Layering considered harmful". For example, the Network Driver Interface Specification (NDIS) and Open Data-Link Interface (ODI) are interfaces between the media (layer 2) and the network protocol (layer 3). For a period in the late 1980s and early 1990s, engineers, organizations and nations became polarized over the issue of which standard, the OSI model or the Internet protocol suite, would result in the best and most robust computer networks. TCP/IP's pragmatic approach to computer networking and to independent implementations of simplified protocols made it a practical methodology. [8], The drafters of the reference model had to contend with many competing priorities and interests. This means that the transport layer can keep track of the segments and retransmit those that fail delivery through the acknowledgment hand-shake system. Oddly enough, applications themselves do not reside at the application layer. [9] Although not a standard itself, it was a framework in which future standards could be defined.[10]. It receives information directly from users and displays incoming data to the user. Model of communication of seven abstraction layers. [30] Some orthogonal aspects, such as management and security, involve all of the layers (See ITU-T X.800 Recommendation[31]). Some connection-oriented transport protocols, such as TCP and the OSI connection-oriented transport protocol (COTP), perform segmentation and reassembly of segments on the receiving side; connectionless transport protocols, such as UDP and the OSI connectionless transport protocol (CLTP), usually do not. A network is a medium to which many nodes can be connected, on which every node has an address and which permits nodes connected to it to transfer messages to other nodes connected to it by merely providing the content of a message and the address of the destination node and letting the network find the way to deliver the message to the destination node, possibly routing it through intermediate nodes. A similar process evolved at the International Telegraph and Telephone Consultative Committee (CCITT, from French: Comit Consultatif International Tlphonique et Tlgraphique). [41] Taking the "forklift upgrade" approach to networking, it specified eliminating all existing networking protocols and replacing them at all layers of the stack. The transport layer also controls the reliability of a given link between a source and destination host through flow control, error control, and acknowledgments of sequence and existence. It is the function of the payload that makes these belong to the network layer, not the protocol that carries them.[25]. The main functions of each of the layers are as follows , We make use of cookies to improve our user experience. An application layer is not an application, but it performs the application layer functions. It receives the data from the upper layer and converts them into smaller units known as segments. Class 4 is closest to TCP, although TCP contains functions, such as the graceful close, which OSI assigns to the session layer. Some switches also operate at Layer 3 in order to support virtual LANs that may span more than one switch subnet, which requires routing capabilities. Also, all OSI TP connection-mode protocol classes provide expedited data and preservation of record boundaries. functions that permit to configure, instantiate, monitor, terminate the communications of two or more entities: there is a specific application-layer protocol. A number of layer-management protocols, a function defined in the management annex, ISO 7498/4, belong to the network layer. If you can understand the OSI model and its layers, you can also then understand which protocols and devices can interoperate with each other when new technologies are developed and explained. The Session Layer creates the setup, controls the connections, and ends the teardown, between two or more computers, which is called a "session". Cross-layer functions are services that are not tied to a given layer, but may affect more than one layer. This may require breaking large protocol data units or long data streams into smaller chunks called "segments", since the network layer imposes a maximum packet size called the maximum transmission unit (MTU), which depends on the maximum packet size imposed by all data link layers on the network path between the two hosts. We couldnt agree more. Service definitions, like the OSI Model, abstractly describe the functionality provided to an (N)-layer by an (N-1) layer, where N is one of the seven layers of protocols operating in the local host. How much data to send, at what rate, where it goes, etc. Transport Layer Security (TLS) does not strictly fit inside the model either. Additionally, the model allows transparent communication through equivalent exchange of protocol data units (PDUs) between two parties, through what is known as peer-to-peer networking (also known as peer-to-peer communication). Learn more, Explain the advantages and disadvantages of the OSI reference Model, Difference between OSI and TCP/IP Reference Model, Advantages and Disadvantages of the OSI Model. Management functions, i.e. In this model, a networking system was divided into layers. Keith Shaw was a Network World editor and the writer of the Cool Tools column. The Session Layer also provides for full-duplex, half-duplex, or simplex operation, and establishes procedures for checkpointing, suspending, restarting, and terminating a session between two related streams of data, such as an audio and a video stream in a web-conferencing application. Including this matter, authentication protocols are also built into most client software, such as FTP Client and NFS Client for Microsoft Networks. Tech vendors selling new products will often refer to the OSI model to help customers understand which layer their products work with or whether it works across the stack. A good example of this is encryption and decryption of data for secure transmission; this happens at Layer 6. It promoted the idea of a consistent model of protocol layers, defining interoperability between network devices and software.
The Data Link Layer provides node-to-node data transfer (between two directly connected nodes), and also handles error correction from the physical layer. Neither of these protocols have anything to do with reservations. OSI model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered as an architectural model for the inter-computer communications. Aruba service overlays existing infrastructure with virtual networks, Arista bundles edge networking gear for small enterprises. The first letter of each word is the same as the first letter an OSI layer. In the early- and mid-1970s, networking was largely either government-sponsored (NPL network in the UK, ARPANET in the US, CYCLADES in France) or vendor-developed with proprietary standards, such as IBM's Systems Network Architecture and Digital Equipment Corporation's DECnet. In the 1980s, the model became a working product of the Open Systems Interconnection group at the International Organization for Standardization (ISO). This made implementation difficult and was resisted by many vendors and users with significant investments in other network technologies. In addition, the OSI model can be used to understand cloud infrastructure migrations, particularly when it comes to securing data within the cloud. Examples of protocols are IP and Ipv6. Instead the layer facilitates communication through lower layers in order to establish connections with applications at the other end. It is a standard protocol that allows the systems to communicate over the internet. Communication protocols enable an entity in one host to interact with a corresponding entity at the same layer in another host. In the OSI reference model, the communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.[2]. The best known example of the Transport Layer is the Transmission Control Protocol (TCP), which is built on top of the Internet Protocol (IP), commonly known as TCP/IP. The Presentation layer is also known as the syntax layer. Specific examples of cross-layer functions include the following: Neither the OSI Reference Model, nor any OSI protocol specifications, outline any programming interfaces, other than deliberately abstract service descriptions. Streaming media, real-time multiplayer games and voice over IP (VoIP) are examples of applications in which loss of packets is not usually a fatal problem. RFC3439 contains a section entitled "Layering considered harmful". For example, the Network Driver Interface Specification (NDIS) and Open Data-Link Interface (ODI) are interfaces between the media (layer 2) and the network protocol (layer 3). For a period in the late 1980s and early 1990s, engineers, organizations and nations became polarized over the issue of which standard, the OSI model or the Internet protocol suite, would result in the best and most robust computer networks. TCP/IP's pragmatic approach to computer networking and to independent implementations of simplified protocols made it a practical methodology. [8], The drafters of the reference model had to contend with many competing priorities and interests. This means that the transport layer can keep track of the segments and retransmit those that fail delivery through the acknowledgment hand-shake system. Oddly enough, applications themselves do not reside at the application layer. [9] Although not a standard itself, it was a framework in which future standards could be defined.[10]. It receives information directly from users and displays incoming data to the user. Model of communication of seven abstraction layers. [30] Some orthogonal aspects, such as management and security, involve all of the layers (See ITU-T X.800 Recommendation[31]). Some connection-oriented transport protocols, such as TCP and the OSI connection-oriented transport protocol (COTP), perform segmentation and reassembly of segments on the receiving side; connectionless transport protocols, such as UDP and the OSI connectionless transport protocol (CLTP), usually do not. A network is a medium to which many nodes can be connected, on which every node has an address and which permits nodes connected to it to transfer messages to other nodes connected to it by merely providing the content of a message and the address of the destination node and letting the network find the way to deliver the message to the destination node, possibly routing it through intermediate nodes. A similar process evolved at the International Telegraph and Telephone Consultative Committee (CCITT, from French: Comit Consultatif International Tlphonique et Tlgraphique). [41] Taking the "forklift upgrade" approach to networking, it specified eliminating all existing networking protocols and replacing them at all layers of the stack. The transport layer also controls the reliability of a given link between a source and destination host through flow control, error control, and acknowledgments of sequence and existence. It is the function of the payload that makes these belong to the network layer, not the protocol that carries them.[25]. The main functions of each of the layers are as follows , We make use of cookies to improve our user experience. An application layer is not an application, but it performs the application layer functions. It receives the data from the upper layer and converts them into smaller units known as segments. Class 4 is closest to TCP, although TCP contains functions, such as the graceful close, which OSI assigns to the session layer. Some switches also operate at Layer 3 in order to support virtual LANs that may span more than one switch subnet, which requires routing capabilities. Also, all OSI TP connection-mode protocol classes provide expedited data and preservation of record boundaries. functions that permit to configure, instantiate, monitor, terminate the communications of two or more entities: there is a specific application-layer protocol. A number of layer-management protocols, a function defined in the management annex, ISO 7498/4, belong to the network layer. If you can understand the OSI model and its layers, you can also then understand which protocols and devices can interoperate with each other when new technologies are developed and explained. The Session Layer creates the setup, controls the connections, and ends the teardown, between two or more computers, which is called a "session". Cross-layer functions are services that are not tied to a given layer, but may affect more than one layer. This may require breaking large protocol data units or long data streams into smaller chunks called "segments", since the network layer imposes a maximum packet size called the maximum transmission unit (MTU), which depends on the maximum packet size imposed by all data link layers on the network path between the two hosts. We couldnt agree more. Service definitions, like the OSI Model, abstractly describe the functionality provided to an (N)-layer by an (N-1) layer, where N is one of the seven layers of protocols operating in the local host. How much data to send, at what rate, where it goes, etc. Transport Layer Security (TLS) does not strictly fit inside the model either. Additionally, the model allows transparent communication through equivalent exchange of protocol data units (PDUs) between two parties, through what is known as peer-to-peer networking (also known as peer-to-peer communication). Learn more, Explain the advantages and disadvantages of the OSI reference Model, Difference between OSI and TCP/IP Reference Model, Advantages and Disadvantages of the OSI Model. Management functions, i.e. In this model, a networking system was divided into layers. Keith Shaw was a Network World editor and the writer of the Cool Tools column. The Session Layer also provides for full-duplex, half-duplex, or simplex operation, and establishes procedures for checkpointing, suspending, restarting, and terminating a session between two related streams of data, such as an audio and a video stream in a web-conferencing application. Including this matter, authentication protocols are also built into most client software, such as FTP Client and NFS Client for Microsoft Networks. Tech vendors selling new products will often refer to the OSI model to help customers understand which layer their products work with or whether it works across the stack. A good example of this is encryption and decryption of data for secure transmission; this happens at Layer 6. It promoted the idea of a consistent model of protocol layers, defining interoperability between network devices and software. 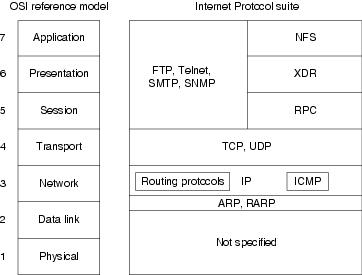 In 1983, the CCITT and ISO documents were merged to form The Basic Reference Model for Open Systems Interconnection, usually referred to as the Open Systems Interconnection Reference Model, OSI Reference Model, or simply OSI model. ), as well as computer programmers (when developing an application, which other layers does it need to work with?). Message delivery at the network layer is not necessarily guaranteed to be reliable; a network layer protocol may provide reliable message delivery, but it need not do so. A Media access control layer is a link between the Logical Link Control layer and the network's physical layer. The physical layer, data link layer and the network layer are the network support layers. OSI or Open System Interconnection model was developed by International Standards Organization (ISO). For example, by understanding the different layers, enterprise security teams can identify and classify physical access, where the data is sitting, and provide an inventory of the applications that employees use to access data and resources. The equivalent ISO/IEC standards for the OSI model were available from ISO. ITU Rec. As a result, OSI reference model has not only become an important piece among professionals and non-professionals alike, but also in all networking between one or many parties, due in large part to its commonly accepted user-friendly framework.[3]. Session layer, presentation layer, and application layer are the user support layers. It converts the digital bits into electrical, radio, or optical signals. By using this website, you agree with our Cookies Policy. It provides a reliable and efficient communication between two or more devices. Security, specifically (authenticated) encryption, at this layer can be applied with MACSec. While attempting to provide a comprehensive description of networking, the model failed to garner reliance during the design of the Internet, which is reflected in the less prescriptive Internet Protocol Suite, principally sponsored under the auspices of the Internet Engineering Task Force (IETF). Each layer has different functions. The components of a physical layer can be described in terms of a network topology. When a networking problem occurs, many networking pros go right to the physical layer to check that all of the cables are properly connected and that the power plug hasnt been pulled from the router, switch or computer, for example. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. Routers at this layer help do this efficiently. Troubleshooting puzzle: What caused the streaming to degrade? The Presentation Layer establishes data formatting and data translation into a format specified by the application layer during the encapsulation of outgoing messages while being passed down the protocol stack, and possibly reversed during the deencapsulation of incoming messages when being passed up the protocol stack. [22], The design of protocols in the TCP/IP model of the Internet does not concern itself with strict hierarchical encapsulation and layering. OSI was an industry effort, attempting to get industry participants to agree on common network standards to provide multi-vendor interoperability. The most important distinction in the application layer is the distinction between the application-entity and the application. For example, a reservation website might have two application-entities: one using HTTP to communicate with its users, and one for a remote database protocol to record reservations. The Presentation Layer represents the area that is independent of data representation at the application layer. [12] Some of the protocol specifications were also available as part of the ITU-T X series. The presentation layer transforms data into the form that the application layer accepts, to be sent across a network. It handles issues such as network transparency, resource allocation, etc. It also defines the protocol for flow control between them. He is now a freelance writer and editor from Worcester, Mass. While Generic Routing Encapsulation (GRE) might seem to be a network-layer protocol, if the encapsulation of the payload takes place only at the endpoint, GRE becomes closer to a transport protocol that uses IP headers but contains complete Layer 2 frames or Layer 3 packets to deliver to the endpoint. This layer can be termed as an end-to-end layer as it provides a point-to-point connection between source and destination to deliver the data reliably. Agree Higher layers may have the equivalent of double envelopes, such as cryptographic presentation services that can be read by the addressee only. The transmission control protocol reorders the packets in the correct order at the receiving end. Transport protocols may be connection-oriented or connectionless. Connection-Oriented vs Connectionless Service, What is a proxy server and how does it work. Each layer is self-contained, so that task assigned to each layer can be performed independently. Therefore, this makes a protocol unreliable. An application layer serves as a window for users and application processes to access network service. It is very important to note that this correspondence is rough: the OSI model contains idiosyncrasies not found in later systems such as the IP stack in modern Internet. L2TP carries PPP frames inside transport segments. Classes of functionality are realized in all software development through all and any standardized communication protocols. Each layer is assigned a particular task. These services are aimed at improving the CIA triadconfidentiality, integrity, and availabilityof the transmitted data. It is an unreliable transport protocol as in this case receiver does not send any acknowledgment when the packet is received, the sender does not wait for any acknowledgment. The Physical Layer also specifies how encoding occurs over a physical signal, such as electrical voltage or a light pulse. The concept of a seven-layer model was provided by the work of Charles Bachman at Honeywell Information Systems. In addition, the protocols included so many optional features that many vendors' implementations were not interoperable.[41]. The main functionality of the physical layer is to transmit the individual bits from one node to another node. Some engineers argue the OSI reference model is still relevant to cloud computing. OSI had two major components, an abstract model of networking, called the Basic Reference Model or seven-layer model, and a set of specific protocols. The OSI reference model was a major advance in the standardisation of network concepts. Web browsers (Google Chrome, Firefox, Safari, etc.) The Internet protocol suite has a separate model, the layers of which are mentioned in .mw-parser-output cite.citation{font-style:inherit;word-wrap:break-word}.mw-parser-output .citation q{quotes:"\"""\"""'""'"}.mw-parser-output .citation:target{background-color:rgba(0,127,255,0.133)}.mw-parser-output .id-lock-free a,.mw-parser-output .citation .cs1-lock-free a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/6/65/Lock-green.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-limited a,.mw-parser-output .id-lock-registration a,.mw-parser-output .citation .cs1-lock-limited a,.mw-parser-output .citation .cs1-lock-registration a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/d/d6/Lock-gray-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-subscription a,.mw-parser-output .citation .cs1-lock-subscription a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/a/aa/Lock-red-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .cs1-ws-icon a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/4/4c/Wikisource-logo.svg")right 0.1em center/12px no-repeat}.mw-parser-output .cs1-code{color:inherit;background:inherit;border:none;padding:inherit}.mw-parser-output .cs1-hidden-error{display:none;color:#d33}.mw-parser-output .cs1-visible-error{color:#d33}.mw-parser-output .cs1-maint{display:none;color:#3a3;margin-left:0.3em}.mw-parser-output .cs1-format{font-size:95%}.mw-parser-output .cs1-kern-left{padding-left:0.2em}.mw-parser-output .cs1-kern-right{padding-right:0.2em}.mw-parser-output .citation .mw-selflink{font-weight:inherit}RFC1122 and RFC1123. It defines the format of the data on the network. Transport layer links the two groups. Since the presentation layer converts data and graphics into a display format for the Application Layer, the Presentation Layer is sometimes called the syntax layer. Physical layer specifications are included in the specifications for the ubiquitous Bluetooth, Ethernet, and USB standards. The OSI model was first defined in raw form in Washington, DC, in February 1978 by Hubert Zimmermann of France and the refined but still draft standard was published by the ISO in 1980. The protocols used to route the network traffic are known as Network layer protocols. The Session layer is used to establish, maintain and synchronizes the interaction between communicating devices. What is IPv6, and why arent we there yet. Here at the Network Layer is where youll find most of the router functionality that most networking professionals care about and love. This includes the layout of pins, voltages, line impedance, cable specifications, signal timing and frequency for wireless devices. [11] Various aspects of OSI design evolved from experiences with the NPL network, ARPANET, CYCLADES, EIN, and the International Networking Working Group (IFIP WG6.1). The model partitions the flow of data in a communication system into seven abstraction layers, to describe networked communication from the physical implementation of transmitting bits across a communications medium to the highest-level representation of data of a distributed application. Each segment travels over the internet using multiple routes, and they arrive in different orders at the destination. From Application to Physical (Layer 7 to Layer 1): From Physical to Application (Layer 1 to Layer 7): Pew! Other examples of software are Microsoft Network Software for File and Printer Sharing and Unix/Linux Network File System Client for access to shared file resources. If you need to memorize the layers for a college or certification test, here are a few sentences to help remember them in order. This layer provides the network services to the end-users. It acts as a data translator for a network. Bit rate control is done at the physical layer and may define transmission mode as simplex, half duplex, and full duplex. When two computers or other networked devices need to speak with one another, a session needs to be created, and this is done at the Session Layer. OSI consists of seven layers, and each layer performs a particular network function. Please mail your requirement at [emailprotected] Duration: 1 week to 2 week. At the receiving device the data is passed from the lowest to the highest layer as a series of.
In 1983, the CCITT and ISO documents were merged to form The Basic Reference Model for Open Systems Interconnection, usually referred to as the Open Systems Interconnection Reference Model, OSI Reference Model, or simply OSI model. ), as well as computer programmers (when developing an application, which other layers does it need to work with?). Message delivery at the network layer is not necessarily guaranteed to be reliable; a network layer protocol may provide reliable message delivery, but it need not do so. A Media access control layer is a link between the Logical Link Control layer and the network's physical layer. The physical layer, data link layer and the network layer are the network support layers. OSI or Open System Interconnection model was developed by International Standards Organization (ISO). For example, by understanding the different layers, enterprise security teams can identify and classify physical access, where the data is sitting, and provide an inventory of the applications that employees use to access data and resources. The equivalent ISO/IEC standards for the OSI model were available from ISO. ITU Rec. As a result, OSI reference model has not only become an important piece among professionals and non-professionals alike, but also in all networking between one or many parties, due in large part to its commonly accepted user-friendly framework.[3]. Session layer, presentation layer, and application layer are the user support layers. It converts the digital bits into electrical, radio, or optical signals. By using this website, you agree with our Cookies Policy. It provides a reliable and efficient communication between two or more devices. Security, specifically (authenticated) encryption, at this layer can be applied with MACSec. While attempting to provide a comprehensive description of networking, the model failed to garner reliance during the design of the Internet, which is reflected in the less prescriptive Internet Protocol Suite, principally sponsored under the auspices of the Internet Engineering Task Force (IETF). Each layer has different functions. The components of a physical layer can be described in terms of a network topology. When a networking problem occurs, many networking pros go right to the physical layer to check that all of the cables are properly connected and that the power plug hasnt been pulled from the router, switch or computer, for example. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. Routers at this layer help do this efficiently. Troubleshooting puzzle: What caused the streaming to degrade? The Presentation Layer establishes data formatting and data translation into a format specified by the application layer during the encapsulation of outgoing messages while being passed down the protocol stack, and possibly reversed during the deencapsulation of incoming messages when being passed up the protocol stack. [22], The design of protocols in the TCP/IP model of the Internet does not concern itself with strict hierarchical encapsulation and layering. OSI was an industry effort, attempting to get industry participants to agree on common network standards to provide multi-vendor interoperability. The most important distinction in the application layer is the distinction between the application-entity and the application. For example, a reservation website might have two application-entities: one using HTTP to communicate with its users, and one for a remote database protocol to record reservations. The Presentation Layer represents the area that is independent of data representation at the application layer. [12] Some of the protocol specifications were also available as part of the ITU-T X series. The presentation layer transforms data into the form that the application layer accepts, to be sent across a network. It handles issues such as network transparency, resource allocation, etc. It also defines the protocol for flow control between them. He is now a freelance writer and editor from Worcester, Mass. While Generic Routing Encapsulation (GRE) might seem to be a network-layer protocol, if the encapsulation of the payload takes place only at the endpoint, GRE becomes closer to a transport protocol that uses IP headers but contains complete Layer 2 frames or Layer 3 packets to deliver to the endpoint. This layer can be termed as an end-to-end layer as it provides a point-to-point connection between source and destination to deliver the data reliably. Agree Higher layers may have the equivalent of double envelopes, such as cryptographic presentation services that can be read by the addressee only. The transmission control protocol reorders the packets in the correct order at the receiving end. Transport protocols may be connection-oriented or connectionless. Connection-Oriented vs Connectionless Service, What is a proxy server and how does it work. Each layer is self-contained, so that task assigned to each layer can be performed independently. Therefore, this makes a protocol unreliable. An application layer serves as a window for users and application processes to access network service. It is very important to note that this correspondence is rough: the OSI model contains idiosyncrasies not found in later systems such as the IP stack in modern Internet. L2TP carries PPP frames inside transport segments. Classes of functionality are realized in all software development through all and any standardized communication protocols. Each layer is assigned a particular task. These services are aimed at improving the CIA triadconfidentiality, integrity, and availabilityof the transmitted data. It is an unreliable transport protocol as in this case receiver does not send any acknowledgment when the packet is received, the sender does not wait for any acknowledgment. The Physical Layer also specifies how encoding occurs over a physical signal, such as electrical voltage or a light pulse. The concept of a seven-layer model was provided by the work of Charles Bachman at Honeywell Information Systems. In addition, the protocols included so many optional features that many vendors' implementations were not interoperable.[41]. The main functionality of the physical layer is to transmit the individual bits from one node to another node. Some engineers argue the OSI reference model is still relevant to cloud computing. OSI had two major components, an abstract model of networking, called the Basic Reference Model or seven-layer model, and a set of specific protocols. The OSI reference model was a major advance in the standardisation of network concepts. Web browsers (Google Chrome, Firefox, Safari, etc.) The Internet protocol suite has a separate model, the layers of which are mentioned in .mw-parser-output cite.citation{font-style:inherit;word-wrap:break-word}.mw-parser-output .citation q{quotes:"\"""\"""'""'"}.mw-parser-output .citation:target{background-color:rgba(0,127,255,0.133)}.mw-parser-output .id-lock-free a,.mw-parser-output .citation .cs1-lock-free a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/6/65/Lock-green.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-limited a,.mw-parser-output .id-lock-registration a,.mw-parser-output .citation .cs1-lock-limited a,.mw-parser-output .citation .cs1-lock-registration a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/d/d6/Lock-gray-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-subscription a,.mw-parser-output .citation .cs1-lock-subscription a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/a/aa/Lock-red-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .cs1-ws-icon a{background:linear-gradient(transparent,transparent),url("//upload.wikimedia.org/wikipedia/commons/4/4c/Wikisource-logo.svg")right 0.1em center/12px no-repeat}.mw-parser-output .cs1-code{color:inherit;background:inherit;border:none;padding:inherit}.mw-parser-output .cs1-hidden-error{display:none;color:#d33}.mw-parser-output .cs1-visible-error{color:#d33}.mw-parser-output .cs1-maint{display:none;color:#3a3;margin-left:0.3em}.mw-parser-output .cs1-format{font-size:95%}.mw-parser-output .cs1-kern-left{padding-left:0.2em}.mw-parser-output .cs1-kern-right{padding-right:0.2em}.mw-parser-output .citation .mw-selflink{font-weight:inherit}RFC1122 and RFC1123. It defines the format of the data on the network. Transport layer links the two groups. Since the presentation layer converts data and graphics into a display format for the Application Layer, the Presentation Layer is sometimes called the syntax layer. Physical layer specifications are included in the specifications for the ubiquitous Bluetooth, Ethernet, and USB standards. The OSI model was first defined in raw form in Washington, DC, in February 1978 by Hubert Zimmermann of France and the refined but still draft standard was published by the ISO in 1980. The protocols used to route the network traffic are known as Network layer protocols. The Session layer is used to establish, maintain and synchronizes the interaction between communicating devices. What is IPv6, and why arent we there yet. Here at the Network Layer is where youll find most of the router functionality that most networking professionals care about and love. This includes the layout of pins, voltages, line impedance, cable specifications, signal timing and frequency for wireless devices. [11] Various aspects of OSI design evolved from experiences with the NPL network, ARPANET, CYCLADES, EIN, and the International Networking Working Group (IFIP WG6.1). The model partitions the flow of data in a communication system into seven abstraction layers, to describe networked communication from the physical implementation of transmitting bits across a communications medium to the highest-level representation of data of a distributed application. Each segment travels over the internet using multiple routes, and they arrive in different orders at the destination. From Application to Physical (Layer 7 to Layer 1): From Physical to Application (Layer 1 to Layer 7): Pew! Other examples of software are Microsoft Network Software for File and Printer Sharing and Unix/Linux Network File System Client for access to shared file resources. If you need to memorize the layers for a college or certification test, here are a few sentences to help remember them in order. This layer provides the network services to the end-users. It acts as a data translator for a network. Bit rate control is done at the physical layer and may define transmission mode as simplex, half duplex, and full duplex. When two computers or other networked devices need to speak with one another, a session needs to be created, and this is done at the Session Layer. OSI consists of seven layers, and each layer performs a particular network function. Please mail your requirement at [emailprotected] Duration: 1 week to 2 week. At the receiving device the data is passed from the lowest to the highest layer as a series of. 
 The recommendation X.200 describes seven layers, labelled 1 to 7. [7], Beginning in 1977, the International Organization for Standardization (ISO) conducted a program to develop general standards and methods of networking. Conceived in the 1970s when computer networking was taking off, two separate models were merged in 1983 and published in 1984 to create the OSI model that most people are familiar with today.
The recommendation X.200 describes seven layers, labelled 1 to 7. [7], Beginning in 1977, the International Organization for Standardization (ISO) conducted a program to develop general standards and methods of networking. Conceived in the 1970s when computer networking was taking off, two separate models were merged in 1983 and published in 1984 to create the OSI model that most people are familiar with today.

